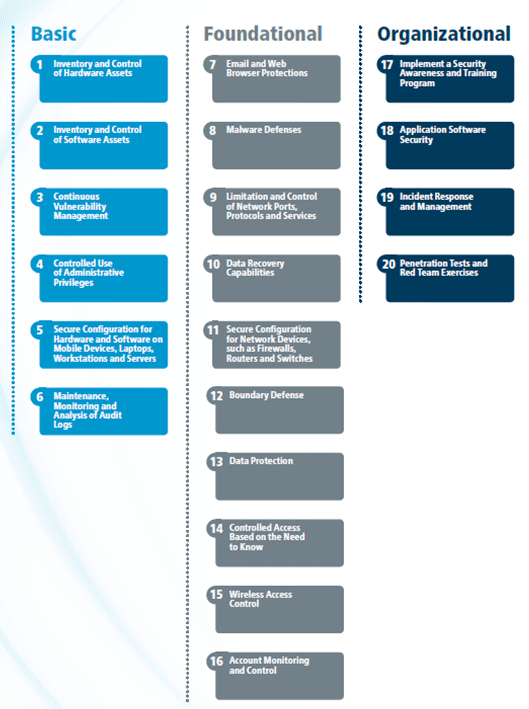
The Critical Security Controls: Basic Cybersecurity Hygiene for your Organization | Qualys Security Blog
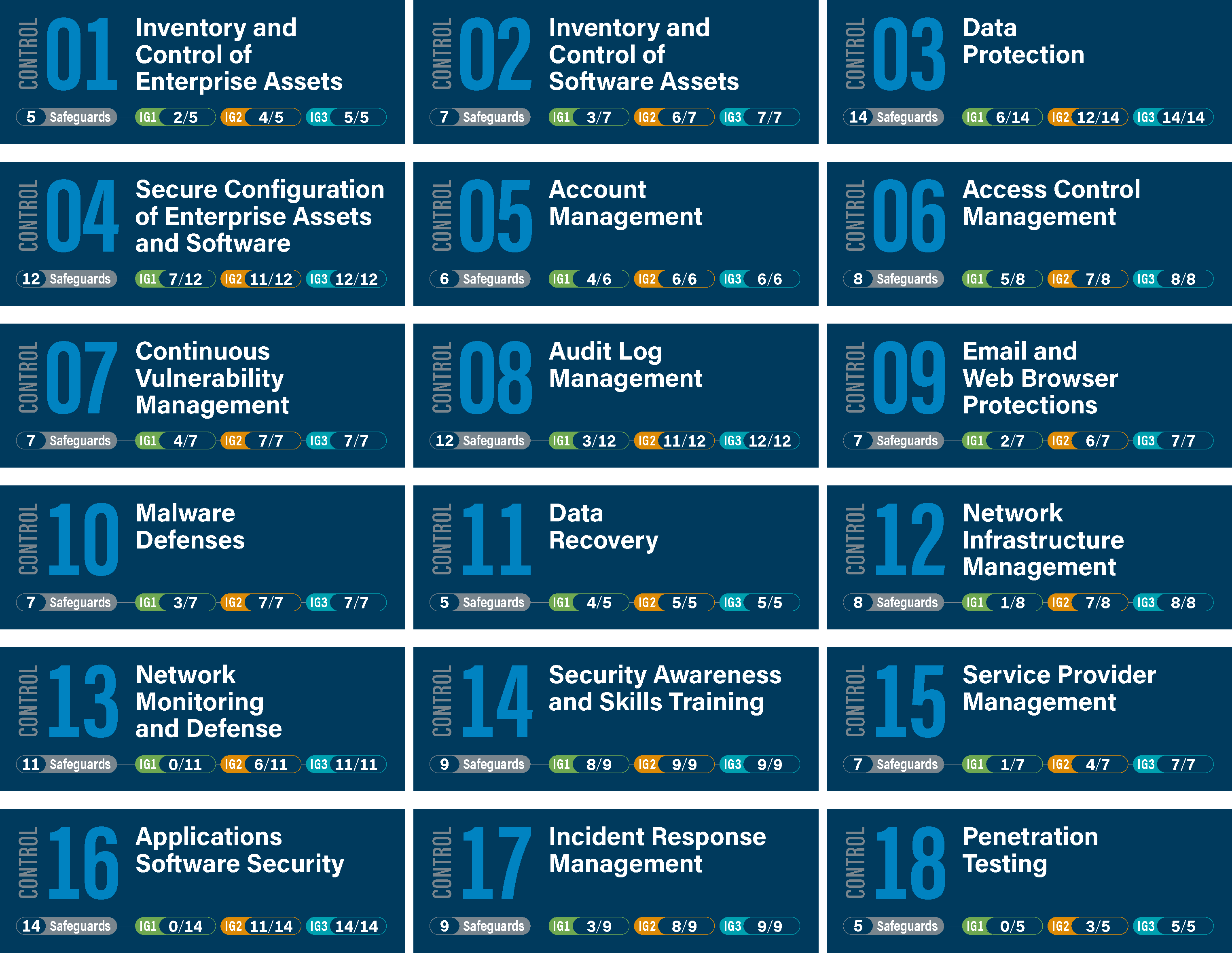
Free Microsoft 365 Assessment Tool based on the top 20 Critical Security Controls from CIS and the Council on Cybersecurity | by Alex Fields | REgarding 365

Implementing the CIS 20 Critical Security Controls: Building Upon Foundational Cyber Hygiene | Qualys Security Blog
Free Microsoft 365 Assessment Tool based on the top 20 Critical Security Controls from CIS and the Council on Cybersecurity | by Alex Fields | REgarding 365

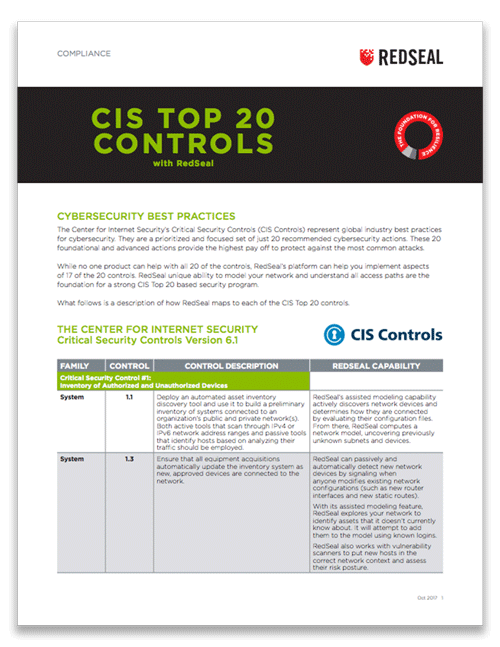
CSA: Cloud Security Alliance - What are the Top 20 Critical Controls for Cloud #ERP Customers? For day 28 of National Cybersecurity Awareness Month read CSA's document to learn the most critical

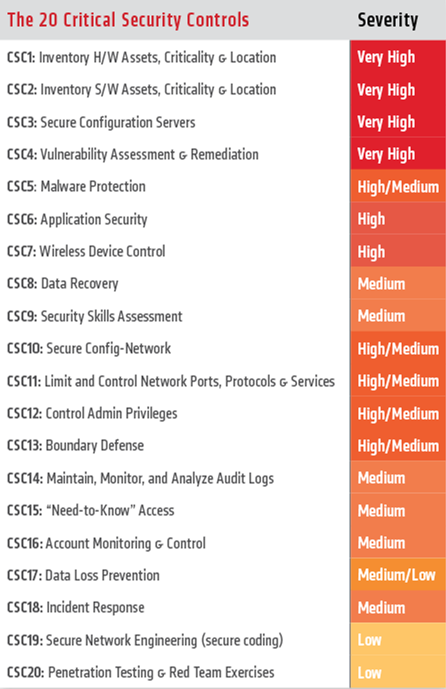
Optiv on Twitter: "Top #CIS Critical #Security Controls help prevent successful #cybersecurity attacks - #PenTest shows #hackers view. https://t.co/aza7HsHXQy https://t.co/JdMxMjGMDZ" / Twitter