![PDF] SandBoxer: A Self-Contained Sensor Architecture for Sandboxing the Industrial Internet of Things | Semantic Scholar PDF] SandBoxer: A Self-Contained Sensor Architecture for Sandboxing the Industrial Internet of Things | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a1f23f8c029e4d496b033db434014316b3269683/4-Figure2-1.png)
PDF] SandBoxer: A Self-Contained Sensor Architecture for Sandboxing the Industrial Internet of Things | Semantic Scholar
![PDF] SandBoxer: A Self-Contained Sensor Architecture for Sandboxing the Industrial Internet of Things | Semantic Scholar PDF] SandBoxer: A Self-Contained Sensor Architecture for Sandboxing the Industrial Internet of Things | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a1f23f8c029e4d496b033db434014316b3269683/4-Figure1-1.png)
PDF] SandBoxer: A Self-Contained Sensor Architecture for Sandboxing the Industrial Internet of Things | Semantic Scholar
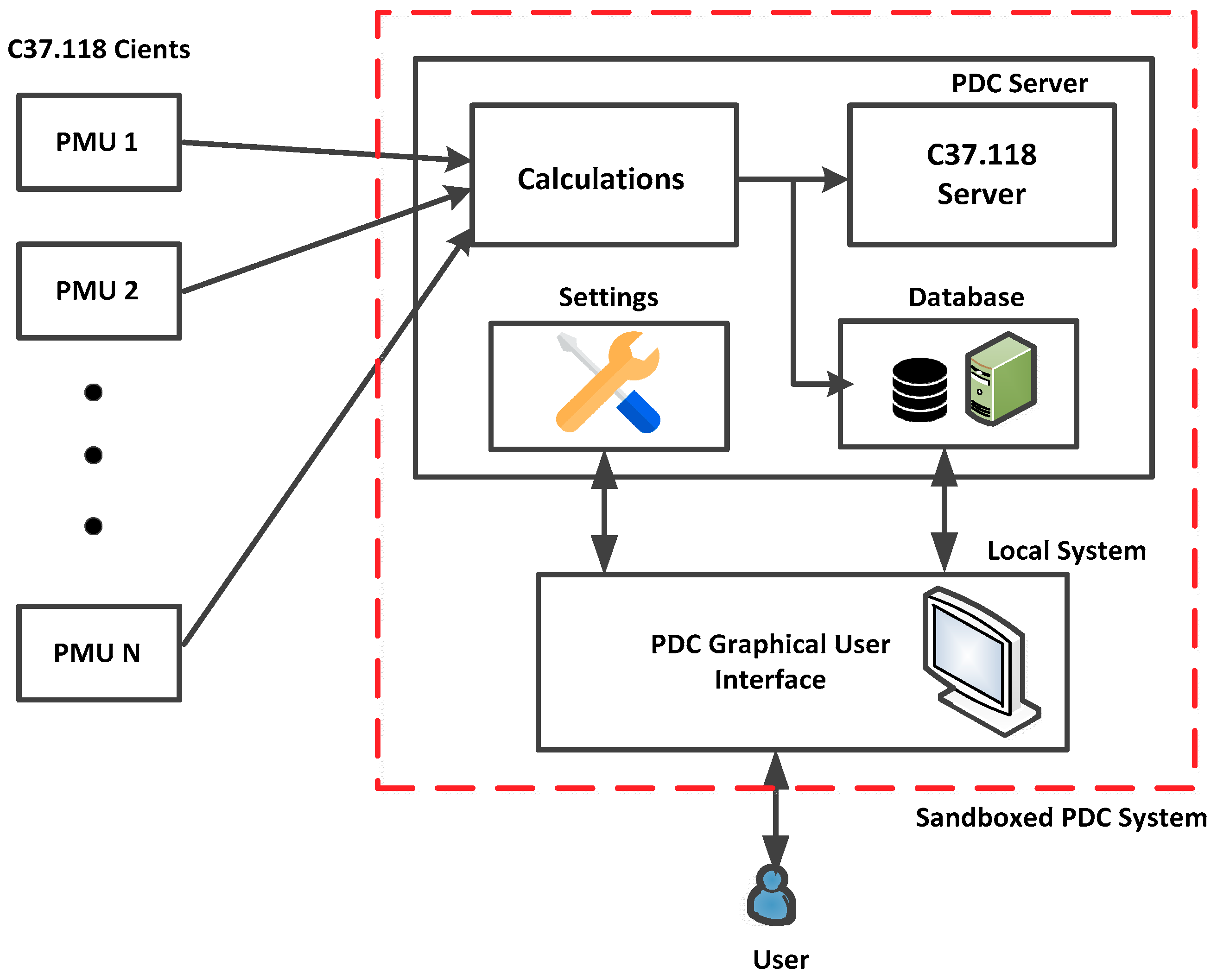
Energies | Free Full-Text | Digital Forensic Analysis of Industrial Control Systems Using Sandboxing: A Case of WAMPAC Applications in the Power Systems